The increasing popularity of social networking has created an emerging avenue for botnet distributors that is rich with potential. Since botnets are a continuing threat, you should be aware of how cybercrooks use them, and how to keep your computer from being part of the problem by not spreading the infection.
The Hook: Cybercriminals create malware designed to infect your machine with "bots", or automated software programs that can execute remote commands, without your knowledge.
They then send out spam emails and instant messages (IM), enticing you to click on a link by mentioning a current news topic or popular artist. If you click on the link, a bot may unknowingly be downloaded onto your computer.
Once your computer is infected, the cybercrook can access and control your computer-and thousands of other infected machines-with the intent of sending spam email, to your friends and family, spreading malware disguised as a personal message from you.
The Latest Methods:
1) Social botnets- Social networking sites like Twitter and LinkedIn provide cybercrooks a simple, yet elusive way to control the bot networks, allowing them to spread spam and malware at will.
For example, it is now possible for cybercrooks to write basic code telling botnets to follow commands given by "@botcommand" on Twitter. To get the botnet to send spam, download a dangerous file, or launch a denial of service attack, all the cybercrook has to do is type in a simple command over Twitter.
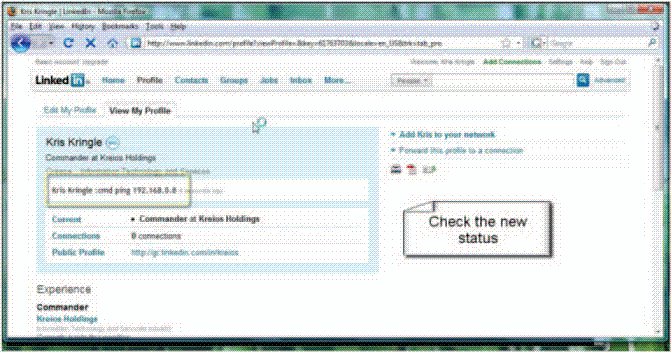
Criminals can send the same kinds of commands on other platforms. On LinkedIn, for example, the cybercrook can create a profile and program bots to follow any command given by that profile. These applications serve solely as a means to send commands, and since they are so widely used and distributed, it is almost impossible to track the cybercrooks.
2) Bot kits-New "exploit kits" are available on the Internet that allow cybercrooks to remotely install software on infected machines and control them through a website. The way it works is pretty clever-the cybercrook simply sends out spam emails or spam instant messages containing links to a website that has the exploit kit installed.
Once the user clicks on the link, the kit determines which exploit to use, based on the user's country, operating system and browser. With the exploit successfully installed, the cybercrook gains remote access to your machine.
3) P2P botnets-Bots controlled by peer-to-peer (P2P) networks are some of the most common botnets we see today. Like social bots, there is no central command, making them difficult to detect. However, they work quite differently. The cybercrook logs onto the P2P network and "pings" the network to see which bots are close by. Responding bots then take commands from a nearby server.
The Dangers: If your computer is part of the botnet, you are unwittingly helping the cybercriminals execute their crimes. Furthermore, your own computer and personal information is at-risk. A cybercrook could instruct the bot to disable your security software or access personal files. And, if your computer is being used to send a lot of spam, it could significantly slow down your machine.
Bottom Line: Cybercriminals continue to come up with new and easy ways to distribute and manage botnets. To avoid being part of the problem, keep your computer protected and learn more about how botnets work.
Tips to Avoid Becoming a Victim:
1. Never click on a link in a spam email or IM from someone you don't know-it might download a bot onto your machine without your knowledge.
2. Turn your computer off when you are not using it - when you are disconnected from the Internet cybercrooks can't access your machine
3. Use comprehensive security software, like McAfee Total Protection(TM) software, to protect you from viruses, spam, and other Internet threats, and keep the software up-to-date.
4. When surfing the web, always use a safe search plug-in, such as McAfee® SiteAdvisor® technology, which warns you of potentially dangerous sites right in your search results
5. Set your operating system and browser to automatically apply updates.
Tips on What to Do If You Have Become a Victim:
You're think your computer is part of a botnet, now what?
1. First, check to see if your Internet connection is inexplicably slow. This might be because the bot is using your connection to send and receive data.
2. If you have a Windows machine, open the network tab under the Task Manager to see if your PC is using the Internet connection, and check to see how much bandwidth it is using. If it is more than a few percent, it is possible you have a bot.
3. If you believe you're infected, disconnect from the Internet modem or router immediately. Reboot your computer in safe mode and run a full virus scan to remove any malicious code.
To sign up to receive alerts by email, please visit: http://home.mcafee.com/...