Unlike sophisticated nation-state actors or established cybercriminal syndicates, these groups demonstrate a distinct operational profile characterized by resource constraints and tactical improvisation. Their technical infrastructure relies predominantly on commodity resources: virtual private servers from budget providers in Vilnius, Tor exit nodes for anonymization, and BitTorrent-based data exfiltration channels. This economic approach to cyber operations indicates actors prioritizing operational security through obscurity rather than technical sophistication.
"The threat landscape is diversifying beyond the actors typically monitored by enterprise security teams," stated Daria Fediay, Chief Executive Officer at CypSec. "These groups represent a hybrid threat, combining traditional organized crime coercive capabilities with accessible cyber tools. Their strategic focus on blackmail and intimidation, rather than financial theft or espionage, creates distinct victim profiles and requires adapted defensive postures."
CypSec's analysis reveals attack patterns consistent with self-taught methodologies derived from publicly available hacking resources. Primary vectors include crafted spear-phishing campaigns targeting personal and professional email accounts, systematic password enumeration against exposed services, and credential harvesting through social engineering. The absence of advanced persistent threat tooling or zero-day exploitation suggests operators without access to commercial cyber weaponry or state-sponsored capabilities.
The geographic concentration in Berlin and Essen, areas with documented clan-related criminal presence, combined with operational patterns in Stockholm's metropolitan region, indicates these networks leverage existing familial and social structures for recruitment, operational security, and victim coercion. Digital compromise frequently serves as precursor to physical intimidation, with stolen data weaponized for blackmail rather than monetization through dark web markets.
This operational model presents unique challenges for conventional cybersecurity frameworks. The human element, victim selection based on social proximity, exploitation of cultural and familial networks, and the psychological impact of combined digital and physical threats, requires integrated defensive strategies addressing both technical vulnerabilities and human risk factors.
Validato AG's late involvement in the investigation underscores the critical intersection of technical threat intelligence and human risk management. The leading Swiss ISO-27001-certified background screening specialist contributed expertise in identifying organizational exposure to actors with criminal affiliations, assessing insider risk indicators, and developing verification protocols for personnel in sensitive positions.
"Technical indicators alone cannot capture this threat category," noted Marco Marti, Validato AG's Chief Technology Officer. "These groups exploit trust relationships, cultural networks, and organizational blind spots in personnel vetting. Our contribution focused on mapping how human risk factors, such as insufficient background verification, inadequate rescreening protocols, and failure to identify conflict-of-interest relationships, create exploitable entry points."
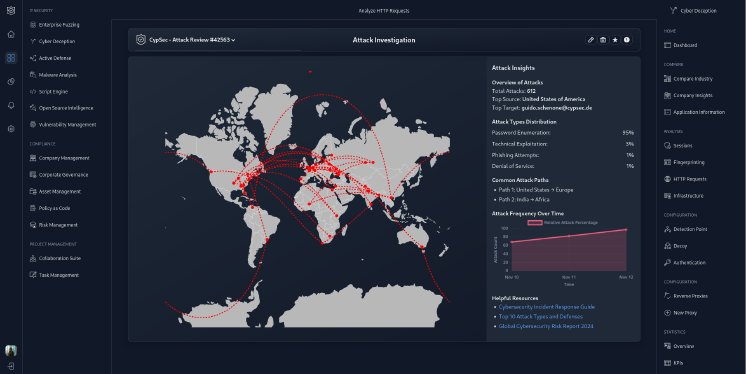
CypSec has developed an interactive intelligence dashboard visualizing identified network connections, infrastructure patterns, and operational timelines. The platform enables security teams to assess organizational exposure, identify potential targeting indicators, and implement proactive defensive measures. The dashboard integrates technical indicators with human risk assessments, providing a unified view of hybrid threats.
The investigation highlights broader implications for European critical infrastructure and government contractors. Traditional security postures optimized for APT actors or financially motivated cybercriminals may prove inadequate against groups prioritizing coercion and leveraging social engineering at scale. Organizations with operations in affected regions, or personnel with connections to targeted communities, face elevated risk requiring tailored defensive strategies.
CypSec and Validato AG are engaging with relevant partners to support ongoing research while providing defensive intelligence to affected organizations. The companies emphasize that effective response requires coordination between technical security teams, human resources functions, and legal/compliance departments, reflecting the hybrid nature of the threat itself. Organizations seeking assessment of their exposure to these threat actors may contact CypSec's threat intelligence division for confidential consultation.