- Technically, it is easier to write malware for Android.
- Currently, better channels exist to distribute for Android malware.
Google has bought Motorola (for the best market perspective on the acquisition, read Fabrizio's take). Consolidation aside, mobile malware is on the rise. For instance, Juniper's malicious Mobile Threat Threats Report found a 400% increase in Android malware since the summer of 2010. According to Paolo Passeri, the number of malware is growing exponentially, and has reached a huge peak in July. This trend is very important for the security industry. A recent Wall Street Journal headline captures the shifting landscape:
Microsoft Faces the Post-PC World Now 25 Years Old, Windows Sales Slow as iPad Gains; Lowest Market Share in Two Decades-82%.
Security translation: make room PC malware, there's a new player in town. The article also notes that in Q2'11, 43% of smartphones were sold with Android. We are already seeing issues: Dasient's recent paper on mobile malware highlighted how applications consistently violate privacy, leaking consumer data to app makers. In their report, they note:
The history of mobile malware continues to be written. After a slow start, the pace of attack is accelerating, and it is possible that we should expect some "mobile malware madness" to occur in the near future, at the very least, if not longer.
What kind of malware can we expect?
The next generation mobile malware is going to be rootkits for mobile. Mobile malware is evolving similarly to how PC malware had evolved. While first-generation PC malware was not sophisticated, in time it achieved a variety of stealthy features: anti-detection, hidden deployment and forensics deletion capabilities. We should expect to see the same in the mobile realm where rootkits for mobile will be hidden from the victim and mobile system processes. In fact, a Proof of Concept was already released in last week's Defcon. The researcher had shown that once the code was installed on an Android phone, the rootkit becomes activated via a phone call or a text message. Since the rootkit runs as a module in Android's Linux kernel, it has the highest level of access to the Android phone and can be a very powerful tool for attackers.
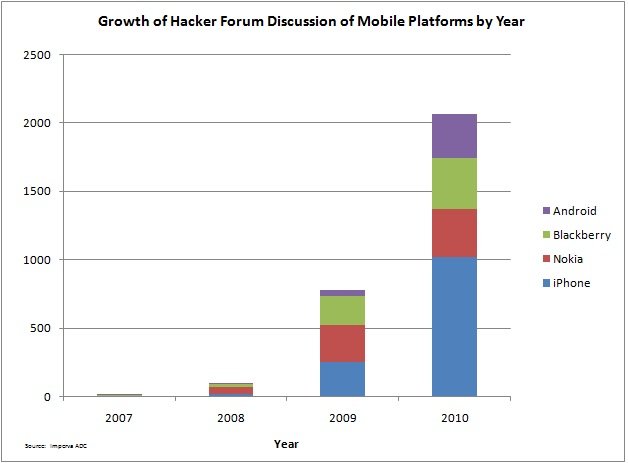
And hackers are taking note. We did an analysis of a hacker forum to determine the frequency that hackers discuss issues around mobile. A simple search over the past few years using iPhone, Android, Nokia and BlackBerry shows a fast-growing fascination.
Though our chart shows more iPhone discussions, we expect this to change.
In this series we'll highlight how Android's distribution model makes it easy to put malware on phones as well as take you through an analysis of a mobile malware. This malware first captures incoming SMS messages before any other system application. It then posts their contents to a drop server. What's unique about this particular malware? The industry has been calling it ZitMo - the mobile equivalent to the notorious PC-based Zeus malware. To be clear, after analyzing this piece of code, the ADC cannot guarantee 100% that this is the Zitmo code, but it seems likely.