Imperva's ADC has a super-geek short analysis of an RTF Stack Buffer Overflow Vulnerability which exploits http://cve.mitre.org/... .
This is a Microsoft problem where .rtf files can be exploited. It's a known vulnerability that was used recently when hackers tried lure people to click on files with false messages about helping Japanese earthquake victims. This exploit spreads malware. Interestingly, the hackers evaded AV and IPS detection.
The vulnerability is a stack-based buffer overflow in Microsoft Office XP SP3, Office 2003 SP3, Office 2007 SP2, Office 2010, Office 2004 and 2008 for Mac, Office for Mac 2011, and Open XML File Format Converter for Mac allows remote attackers to execute arbitrary code via crafted RTF data, aka "RTF Stack Buffer Overflow Vulnerability.
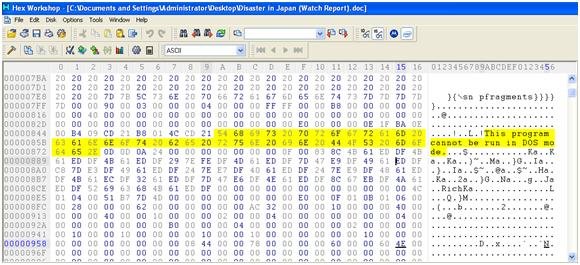
By opening the .doc file with your favorite hex editor it is possible to see at the beginning of the file the following header stub:'rtf1{this document is more important!\par please keep it private.'
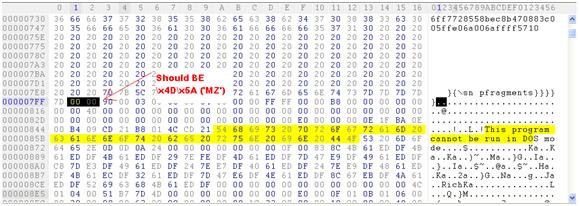
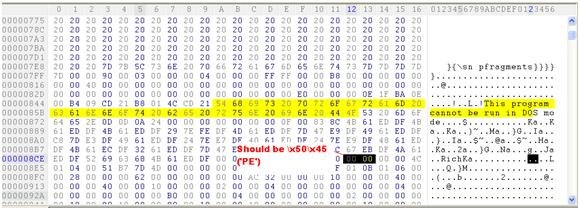
Yep, the MS-DOS stub message "This program cannot be run in DOS mode" which definitely indicates an embedded executable.Nice, but where are MZ and PE headers? At offset 0x0000084E we can find \x00\x00 instead of \x4D\x5A ('MZ') and at offset 0x000008E0, again, we can find \x00\x00 instead of \x50\x45 ('PE').
The "MZ" and the "PE" are headers associated with executables. The PE sections are created automatically by the programmer's compiler or assembler. The purpose of the Disk Operating System (DOS) MZ header is so DOS will recognize the program. The PE header contains several fields used by the PE loader. When a program gets executed on an OS that can process the PE file format, the PE loader uses the DOS MZ header to find the starting offset of the PE header (by skipping the DOS stub).
The main reason for not including them is for bypassing IPS / AV.
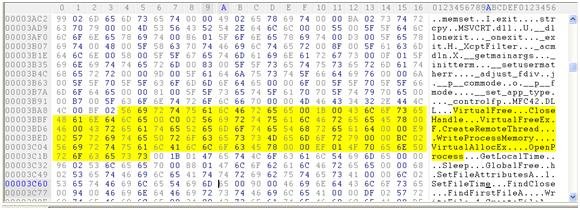
Diving deeper will reveal some more strings that indicate for an embedded executable:
OpenProcess (Retrieves a HANDLE to the remote process) ....VirtualAllocEx (Allocate memory for the DLL name in the remote process) ....WriteProcessMemory(Write the DLL name, including full path, to the allocated memory)....CreateRemoteThread (Map your DLL to the remote process)....
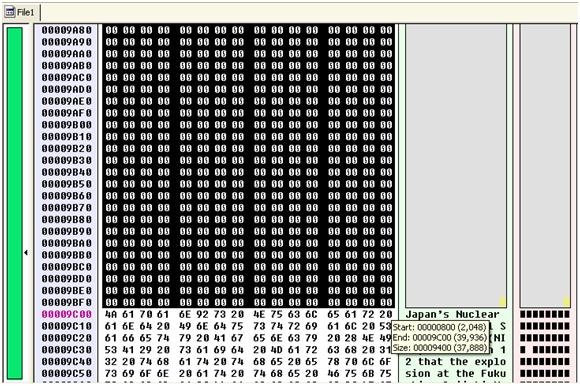
Hmm, looks like process code injection, probably a DLL will join the party later on. Now, let's add the missing headers, dump the embedded exe file and see what it does. In order to dump the exe file we must start dumping from offset 0x00000800 to 0x00009C00 which will get us 37888 bytes of malicious code.
When saving as an executable we named Trojan.exe. The Trojan.exe's general Info:
- MD5 : 5ABD60F270B7169685DBC9E9E66A3734SHA1
- 2586D808938ADF8D819A238080B20C34DC0FF294CRC32
- 0x7B7F6F91
Trojan.exe Analysis
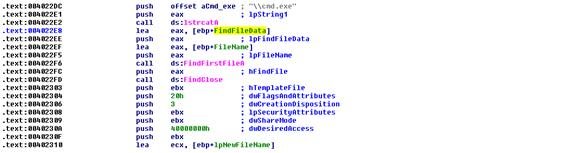
Once executed the Trojan adds a copy of itself under C:\WINDOWS\system32. It extracts cmd.exe file attributes and sets them with the new copy of the Trojan under system32.
- It suspends the execution of the current thread for 100 milliseconds. (Sleep function).
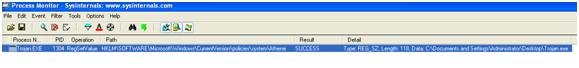
- By using RegCreateKeyExA function it sets the following registry path: 'SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\Athene' with the following value [Original File path]\Trojan.exe.
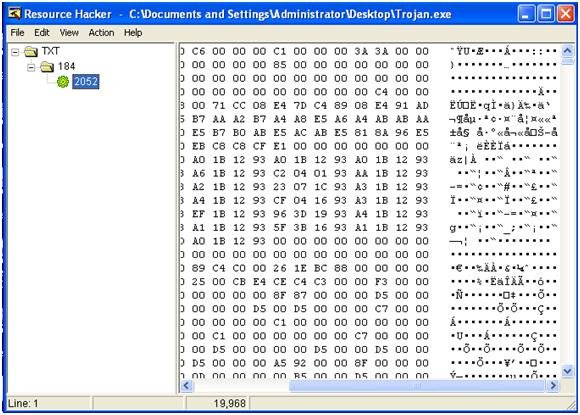
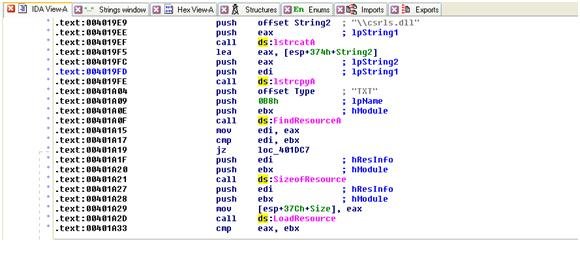
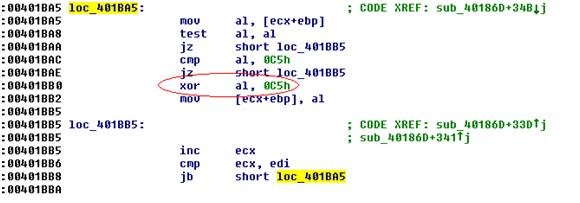
The DLL gets deobfuscated by XORing its bytes with 0xC5. The "TXT" resource is saved as csrls.dll and the Trojan sets its timestamps to match calc.exe timestamps.
The Deobfuscation Function:
csrls.dll Analysis:
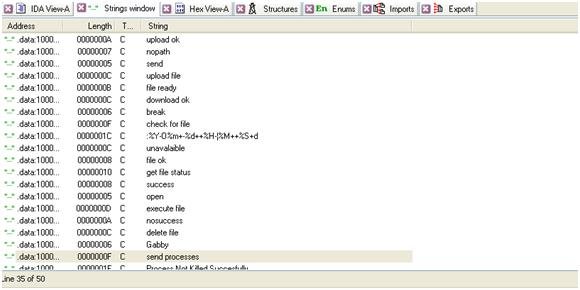
Let's create a copy of csrls.dll, name it as copy.dll and open it with IDA. Check out some interesting strings:
By Googling some of the strings ("Gabby" , "Check for file".....) you can find a very interesting open source project on http://www.codeproject.com called "Network Administrator" which was written at 2004 and shows how you can work with a multithreading client server application and administrate computers on a network.
http://www.codeproject.com/...
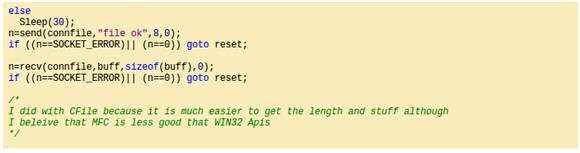
By looking at its code it is possible to notice the same above strings just in "human readable" view:
In other words, embedded is the project for getting a remote shell project!