Lawrence Orans, research director at Gartner, provided additional commentary on how to analyse and compare different approaches and select complementary (as opposed to overlapping) solutions for detecting ATAs and malware.
"The traditional defence-in-depth components are still necessary, but are no longer sufficient in protecting against advanced targeted attacks and advanced malware," said Mr Orans. "Today's threats require an updated layered defence model that utilises "lean forward" technologies at three levels: network, payload (executables, files and Web objects) and endpoint. Combining two or all three layers offers highly effective protection against today's threat environment.
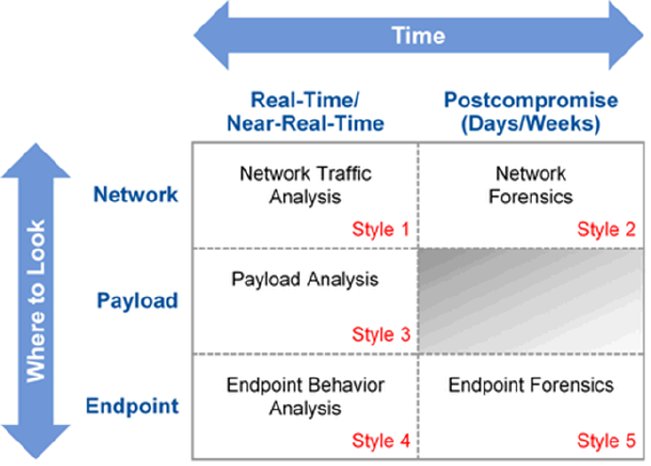
To help security managers select and deploy the most-effective APT defence technologies, Gartner has developed the Five Styles of Advanced Threat Defence Framework. This framework is based on two dimensions: where to look for ATAs and malware (the rows), and a time frame for when the solution is most effective (the columns). The dashed lines between styles represent "bleed-through," since many vendor solutions possess characteristics of adjacent styles.
Style 1 - Network Traffic Analysis
This style includes a broad range of techniques for Network Traffic Analysis. For example, anomalous DNS traffic patterns are a strong indication of botnet activity. NetFlow records (and other flow record types) provide the ability to establish baselines of normal traffic patterns and to highlight anomalous patterns that represent a compromised environment. Some tools combine protocol analysis and content analysis.
Style 2 - Network Forensics
Network Forensics tools provide full-packet capture and storage of network traffic, and provide analytics and reporting tools for supporting incident response, investigative and advanced threat analysis needs. The ability of these tools to extract and retain metadata differentiates these security-focused solutions from the packet capture tools aimed at the network operations buyer.
Style 3 - Payload Analysis
Using a sandbox environment, the Payload Analysis technique is used to detect malware and targeted attacks on a near-real-time basis. Payload Analysis solutions provide detailed reports about malware behaviour, but they do not enable a post compromise ability to track endpoint behaviour over a period of days, weeks or months. Enterprises that seek that capability will need to use the incident response features of the solutions in Style 5 (Endpoint Forensics). The sandbox environment can reside on-premises or in the cloud.
Style 4 - Endpoint Behaviour Analysis
There is more than one approach to Endpoint Behaviour Analysis to defend against targeted attacks. Several vendors focus on the concept of application containment to protect endpoints by isolating applications and files in virtual containers. Other innovations in this style include system configuration, memory and process monitoring to block attacks, and techniques to assist with real-time incident response. An entirely different strategy for ATA defence is to restrict application execution to only known good applications, also known as "whitelisting".
Style 5 - Endpoint Forensics
Endpoint Forensics serves as a tool for incident response teams. Endpoint agents collect data from the hosts they monitor. These solutions are helpful for pinpointing which computers have been compromised by malware, and highlighting specific behaviour of the malware.
Because of the challenges in combating targeted attacks and malware, security-conscious organisations should plan on implementing at least two styles from this framework. The framework is useful for highlighting which combinations of styles are the most complementary. Effective protection comes from combining technologies from different rows (for example: network/payload, payload/endpoint or network/endpoint). The same logic applies to mixing styles from different columns (different time horizons). The most effective approach is to combine styles diagonally through the framework. For example, some useful combinations of styles follow.
More detailed information on the framework and how security managers can select and deploy the most effective APT defence technologies can be found in the report "Five Styles of Advanced Threat Defence". The report can be found on Gartner's web site at http://www.gartner.com/....
Mr Orans will provide additional insight into cybersecurity at Gartner Symposium/ITxpo 2013 taking place October 6-10 in Orlando, Florida.
About Gartner Symposium/ITxpo
Gartner Symposium/ITxpo is the world's most important gathering of CIOs and senior IT executives. This event delivers independent and objective content with the authority and weight of the world's leading IT research and advisory organization, and provides access to the latest solutions from key technology providers. Gartner's annual Symposium/ITxpo events are key components of attendees' annual planning efforts. IT executives rely on Gartner Symposium/ITxpo to gain insight into how their organizations can use IT to address business challenges and improve operational efficiency.