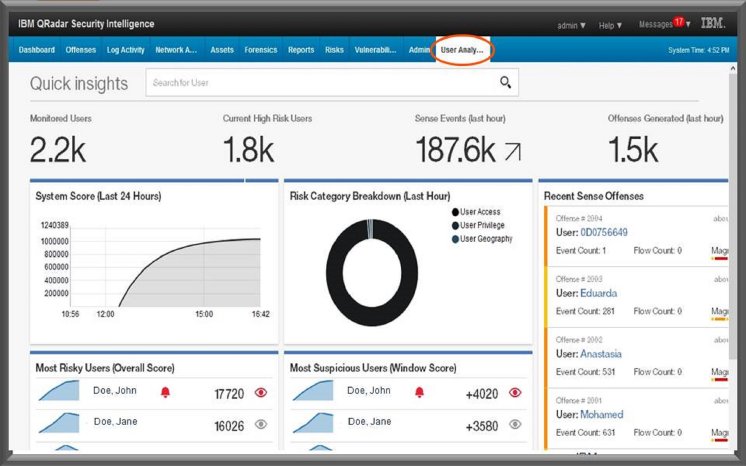
Insider threats are currently responsible for 60 percent of attacks facing businesses, but roughly a quarter of these attacks are the result of users’ credentials falling into the hands of hackers via employees, contractors or partners who are tricked by malware-laden phishing attacks or other techniques1. For example, the new user behavior analytics app would alert analysts to a user logging into a high value server for the first time, from a new location, while using a privileged account. This change in pattern would be identified because the IBM QRadar User Behavior Analytics solution created a baseline of normal user behavior for this employee and detected a significant deviation.
“Organizations need a better way to protect themselves against insider threats – whether they be from inadvertent actors or malicious cybercriminals with access to an organization’s inner workings and technology systems,” said Jason Corbin, Vice President of Strategy and Offering Management, IBM Security. “This new app provides analysts with the ability to quickly pivot by using existing cybersecurity data to see the early warning signs that are often buried in suspicious user activities, ultimately helping them more consistently address breaches before they occur.”
IBM QRadar User Behavior Analytics leverages data from customers’ existing QRadar investment giving them a single platform to analyze and manage security events and data. This integration saves security analysts from having to reload and curate data from multiple platforms to identify and investigate user behavior side-by-side with other indicators of compromise QRadar detects. The solution helps security professionals guard against malicious threats through:
- Risk Analysis Profiles – the app analyzes risky user actions and applies a score to anomalous behaviors helping to identify both potential rogue insiders and suspected cybercriminals using compromised credentials.
- Prioritized Behavioral Analysis Dashboard – analysts can gain better visibility and understanding of actions that lead a user to open up a malicious document or how they gained escalated privileges. A single mouse click, or an attachment or link in a phishing email, for example, can add suspicious user activity to a watch list or permit a text-based annotation to explain the analyst’s observations.
- Enhancing Existing QRadar Security Data – with user information pulled from the entire IT environment, security teams will be able to tap into the existing broad set of data sources and threat intelligence in QRadar to detect threats across users and assets.
Over the past two years, IBM has made significant moves to help security professionals worldwide collaborate to achieve an advantage over cybercriminals, including opening its 700 TB of threat data to the public with the launch of IBM X-Force Exchange. Built on X-Force Exchange intelligence, the IBM Security App Exchange has developed into an expansive online marketplace for partners and customers to share and download apps based on IBM Security technologies, such as IBM QRadar. The marketplace features dozens of 3rd party solutions to further clients’ ability to customize their security environment using IBM’s open platform approach.
About IBM Security
IBM Security offers one of the most advanced and integrated portfolios of enterprise security products and services. The portfolio, supported by world-renowned IBM X-Force® research, enables organizations to effectively manage risk and defend against emerging threats. IBM operates one of the world’s broadest security research, development and delivery organizations, monitors 20 billion security events per day in more than 130 countries, and holds more than 3,000 security patents. For more information, please visit www.ibm.com/security, follow @IBMSecurity on Twitter or visit the IBM Security Intelligence blog.
1IBM X-Force Cyber Threat Index, 2016
http://www-03.ibm.com/press/us/en/pressrelease/50241.wss